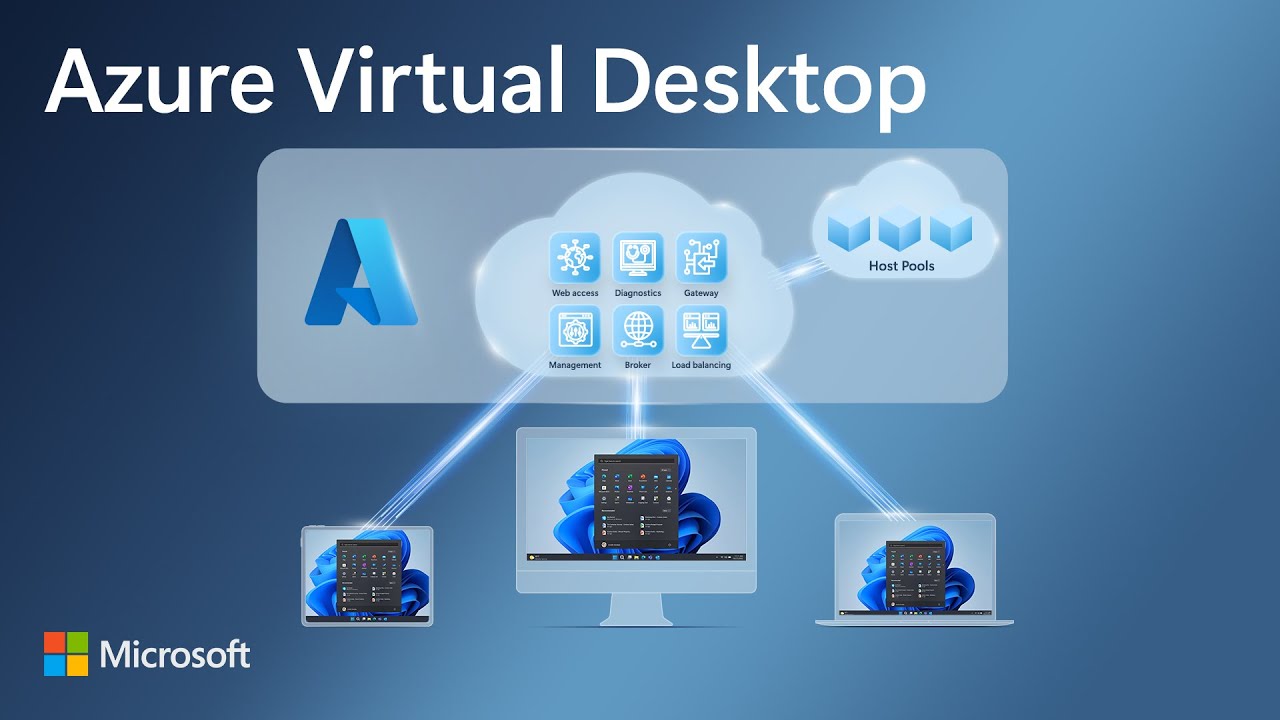
Crash Course in Microsoft Purview
With ChatGPT and other AI-powered productivity applications in use in corporate America, companies need to pay attention to the data that is flowing through those AI applications. Safeguarding sensitive data requires a data management and governance plan. In this e-book, you'll learn how the Microsoft Purview data management platform delivers. Download and read the eBook and learn about Purview's platform-based approach that enables information protection, data governance, risk management, and compliance across multicloud, multiplatform data estates.